Adwind: a remote access Trojan delivered via Spam Campaign
- Details
- Category: Social Engineering
- Published: Thursday, 13 July 2017 11:04
Written by Alan Ferrari, SUPSI and Enrico Frumento, CEFRIEL
Nowadays, cybercriminals are becoming dramatically more adept, innovative, and stealthy (only 117.649 variants of this specific attack have been seen). The new trends have moved to novel techniques that come with limitless attack vectors, support for cross platforms and low detection rates (source: TrendMicro).
Recently that Adwind, (a java-based notorious cross-platform Remote Access Trojan), has re-emerged and is used to target enterprises in the aerospace industry, mostly located in Switzerland, Austria, Ukraine, and the US.
Recently, security researchers discovered that Adwind (a.k.a: AlienSpy, Frutas, jFrutas, Unrecom, Sockrat, JSocket, and jRat is capable of infecting all the major operating systems, including Windows, Mac, Linux, and Android, and it includes a wide variety of capabilities including stealing credentials, keylogging, taking pictures or screenshots, data gathering and exfiltrate data. It can also turn the machines into botnets to carry out DDoS attacks or turn infected machines into bitcoin miner.
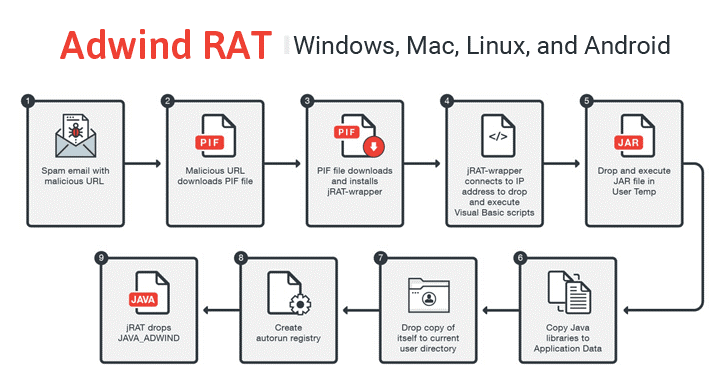
Figure 1 Adwind attack pipeline
Adwind attack pipeline is illustrated in Figure 1. An interesting feature is the method of delivery (Box 1 and 2 in Figure 1), that is based on human factor, a quite classical social engineering hook. According to TrendMicro, the phishing campaign is deployed in two waves and is a classic example of social engineering. The first has been observed on June 7, 2017 and it uses a different URL to divert victims to theirs NET-written malware equipped with spyware capabilities. The second wave was observed on June 14 and used different domains that hosted their malware and command and control (C&C) servers. Both waves apparently employed a similar social engineering tactic to lure victims into clicking the malicious URLs.
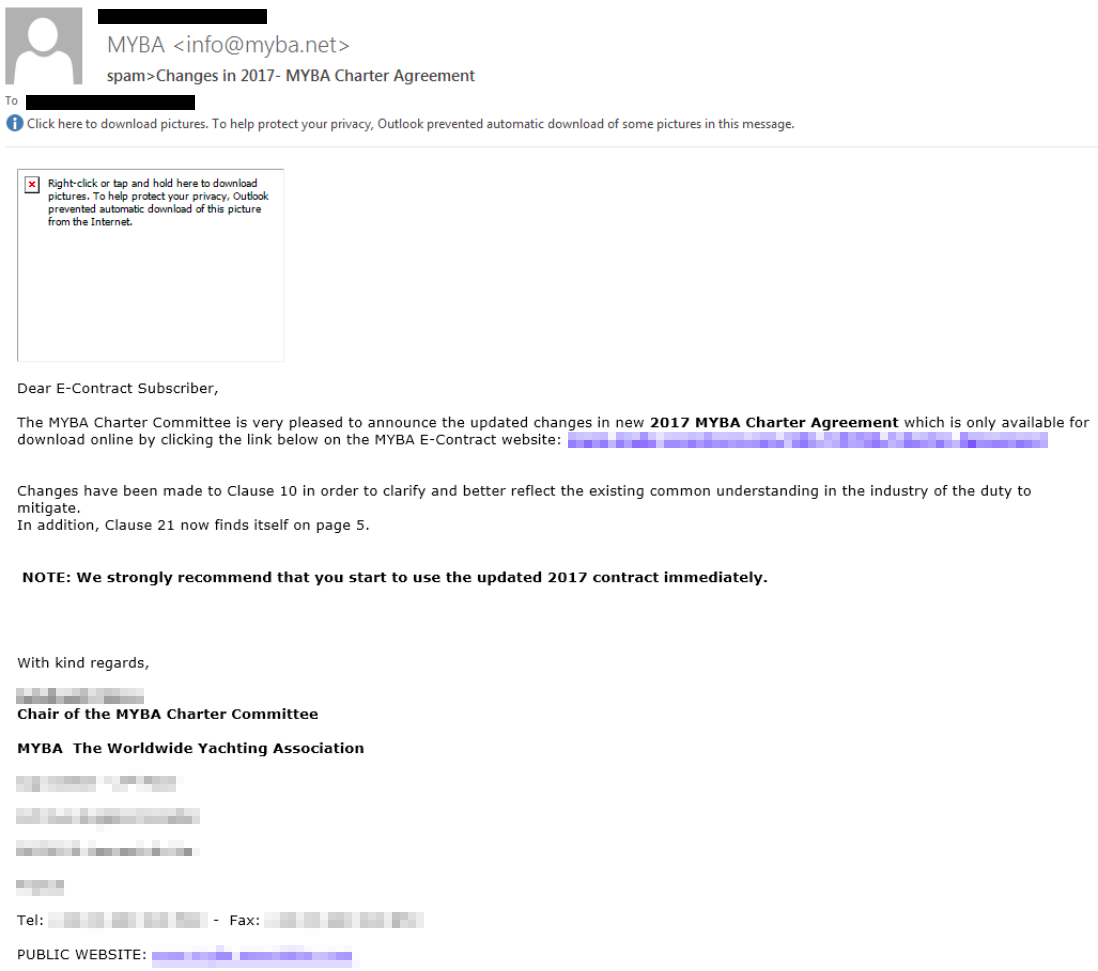
Figure 2 Adwind Spam e-mail
The spam email’s message (Figure 2) impersonates the chair of the Mediterranean Yacht Broker Association (MYBA) Charter Committee. The subject line (“Changes in 2017 – MYBA Charter Agreement”) tries to imprint the sense of urgency to the potential victims. The attacker uses a forged sender address, (info[@]myba[.]net) and an almost ”legitimate” content to convince the victim to click the URL. No details have been released about the type of employees involved, but the specific type of hook indicates that a study of the victims’ context was performed in advance. This type of attacks usually has a very long passive phase of preparation, which includes harvesting and investigation of the victim’s dataspace: investigation of the digital shadow of the enterprise, through OSINT (Open Source intelligence); IMINT (Imagery intelligence); HUMINT (Human intelligence); SIGINT (Signals Intelligence).
Summing up the phases 1 and 2 of the Figure 1 can be further expanded into a more complex set of actions, all of them usually conduct passively. Which means without awareness of the victim.
- Segmentation of the Enterprise asset dataspace and identification of the most valuable “sections”
- Decision and behavioural processes analysis
- Identification of the Super Targets in the Enterprise (those that are, by their nature, more easily than others falling into phishing or scam)
- Identification of the keyholders of the most valuable assets
- Personality profiling of the victims
- Identification of the Cognitive processes (e.g. language register, hot topics, sentiment analysis, …)
- Create the attacks around the personality or emotional status (e.g., https://www.weforum.org/agenda/2016/11/why-being-extremely-happy-might-be-a-bad-thing)
Social engineering is the key and the winning element of Adwind but in general of almost any modern malware. This highlights the importance of the work we are currently carrying out in the DOGANA project.
Sources
- http://blog.trendmicro.com/trendlabs-security-intelligence/spam-remote-access-trojan-adwind-jrat/
- https://amp.thehackernews.com/thn/2017/07/adwind-rat-malware.html
- http://thehackernews.com/2013/02/cross-platform-trojan-builder.html
by Alan Ferrari (SUPSI) and Enrico Frumento (CEFRIEL)





