Multi-layer defence against SE: evolution and evaluation
- Details
- Category: Social Engineering
- Published: Wednesday, 09 November 2016 17:31
Written by Carlo Dambra, PROPRS and Enrico Frumento, CEFRIEL
The idea of a multi-layer defence against cyber-attacks appeared in a SANS whitepaper [1] in 2003 but at the time it was mainly referring to technological defences. Anyhow, the idea was to apply a series of coordinated defences to protect against cyber-attacks: security policy, perimeter router hardening, firewall, antivirus software, network switches, IDS, employees training, physical security and patch management.
As explained several times within this Blog, the cyberattacks, initially targeting only the computers, have evolved to include also the Social Engineering (SE) attacks, thus targeting humans: today SE is the main-stream way to start an attack. The Figure 1 reports an interpretation of the statistics reported by the APWG (Anti Phishing Working Group) for the Q2 of 2016.
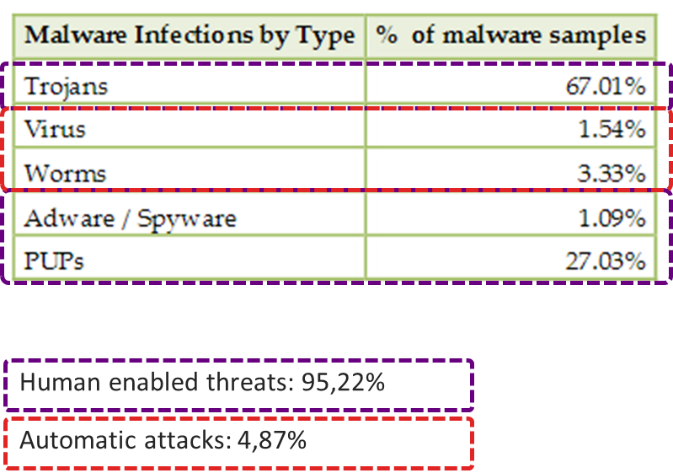
Situation in 2016 (Q2.2016) of attacks. Source: "Phishing activity trends report unifying the global response to Cybercrime," AntiPhishing Working Group (APWG), Oct. 3, 2016. [Online]. Available: http://docs.apwg.org/reports/apwg_trends_report_q2_2016.pdf
Multi-layer defence approaches have followed this evolution [2] considering five layers: network controls, antivirus, reputation, behavioural analysis and detection and remediation.
The approach has recently led to the appearance of the first integrated commercial products and, in particular, the layered solution by IRONSCALES based on four layers:
- Awareness, building awareness via assessment and training.
- Detection, using automated phishing detection tools.
- Mitigation, based on deep forensics and 1-click mitigation response for the SOC team.
- Federation, by real-time anonymous sharing of phishing incidents across organisations, implementing a sort of Human Sensor Network [3].
Despite these evolutions, it is still possible to quite easily bypass these systems using a targeted attack with the right knowledge of the target. All these multi-layered systems are using an AI-boosted mix of syntax, semantics and human reasoning models derived from the cognitive sciences such as Bayesian models of thinking.
A complex human attack vector then should therefore hide itself from these detection solutions using the same reasoning of the defender:
- Syntactically, not triggering any deep inspection rule, i.e. using ad-hoc domain without suspect/know terms of typos like the real mails.
- Semantically, this may be definitely more complex because the semantics of the memes is something that needs a deep knowledge of your victims. But the complexity is human rather than technological, because it is a matter of creating the right message. The more the phish mail resembles a real mail the more the detection system would fail. After all these systems are made to filter out phishing mail only, but what if the phish email become semantically almost identical to the real emails?
It is interesting to report what stated in [4]: “Today’s security systems usually fall into one of two categories: man, or machine. So-called “analyst-driven solutions” rely on rules created by human experts and therefore miss any attacks that don’t match the rules. Meanwhile, today’s machine-learning approaches rely on “anomaly detection,” which tends to trigger false positives that both create distrust of the system and end up having to be investigated by humans, anyway”.
The nature of the problem lies inside the solution: the AI-enabled reasoners learn to distinguish real vs fake emails using samples provided by either experts or users and applying to these samples a syntactic + semantic interpretation of the text, followed by a deep-inspection of all the mail metadata and links. Thanks to this strategy, they detect much more phishing than any other method. But, evasion attacks exist: a context aware phishing is made to be almost identical to real emails, except few tiny differences, and often can slip out of the checks (e.g., the paper [5]). Despite AI-reasoners can understand personal writing styles (e.g. through stylometry)[6], the complexity and number of false positive/negative are still high for the adoption into the Enterprises.
This attack strategy is already starting to appear in the real attacks as demonstrated by the early samples of multi-stages SE attacks. This is an area of improvement for attackers and DOGANA is expecting more samples in this direction.
[1] Wescoat, "Different Layers in Defense in Depth," SANS Institute, Dec. 2, 2003. [Online]. Available: https://www.giac.org/paper/gsec/3520/layers-defense-in-depth/105736
[2] Shenk, "Layered Security: Why It Works," SANS Institute, Dec. 2013. [Online]. Available: https://www.sans.org/reading-room/whitepapers/analyst/layered-security-works-34805
[3] Powers, "Establishing a human sensor network," in SANS Security Awareness Blog, 2015. [Online]. Available: https://securingthehuman.sans.org/blog/2015/07/06/establishing-a-human-sensor-network-secawaresummit
[4] "AI system predicts cyber attacks using input from human experts," Help Net Security, 2016. [Online]. Available: https://www.helpnetsecurity.com/2016/04/19/ai-system-predicts-cyber-attacks/
[5] Biggio et al., "Evasion attacks against machine learning at test time," in Machine Learning and Knowledge Discovery in Databases. Springer Science + Business Media, 2013, pp. 387–402. [Online]. Available: http://www.ecmlpkdd2013.org/wp-content/uploads/2013/07/527.pdf. Accessed: Oct. 19, 2016.
[6] Individuals have unique writing styles because language is learned on an individual basis. Stylometry is the study of attributing authorship to documents based only on the linguistic style they exhibit. “Linguistic Style” Features: sentence length, word choices, syntactic structure, etc. [7]
[7] Caliskan-Islam, "De-anonymization and Machine Learning’s Role in Privacy and Security," in Building trust in the information age Summer School on computer security and privacy, University of Cagliari, 2016. [Online]. Available: https://comsec.diee.unica.it/summer-school/program.html#2. Accessed: Oct. 19, 2016.
by Carlo Dambra (PROPRS) and Enrico Frumento (CEFRIEL)





