The real story behind the latest Pawn Storm attack and the Windows zero-day patch release
- Details
- Category: Social Engineering
- Published: Thursday, 10 November 2016 08:56
Written by Enrico Frumento, CEFRIEL
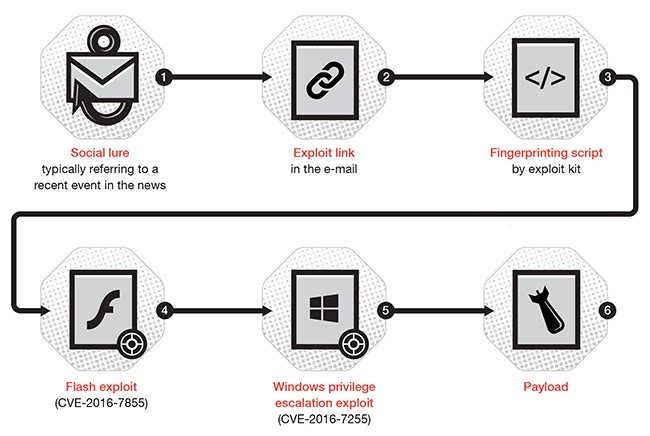
* Image source: http://blog.trendmicro.com/trendlabs-security-intelligence/pawn-storm-ramps-up-spear-phishing-before-zero-days-get-patched/
Recently the news reported an interesting new sample of a type of attacks that we know very well. This one is specifically interesting because of the structure of the attack: if you look at the process reported below, the process follows some interesting steps: a social engineering lure (a quite efficient one as usual from Pawn Storm OCG) is followed by a drive-by-infection and an ad-hoc malware, crafted by a malware forgery, after a fingerprinting of the victim's machine [1].
This structure follows exactly the same type of attacks the DOGANA project is considering and nowadays it is also quite mainstream, among the most complex attacks (those done by the elite OCG).
The social engineering lure as said before was quite well done. See below.
Some of the e-mails posed as an invitation for a “Cyber Threat Intelligence and Incident Response conference in November” by Defense IQ. The email contained a RTF document named “Programm Details.doc,” which contained an embedded Flash file that downloaded a Flash exploit for the just-patched CVE-2016-7855.
However, the interesting part is that of the commentary focuses just on the resolution by Microsoft of the technical exploit (the 0day Flash vulnerability) without realiIng that an attack structure like that is flexible enough to not care about which 0day is actually used to infect the victims (well this one was even suggested by Google's insane patch release policy). The 0days are just commodities added into a more flexible and deadliest structure.
- Thanks to flexible and efficient social engineering to find victims is not a problem, as we discussed in this blog already
- Fingerprinting allows to find tons of machines still vulnerable to the same vulnerability or even older ones. A previous paper, from TrendMicro about a past Pawn Storm attack, clearly shows the efficiency of this structure [2]
- The presence of an efficient malware forgery ensure years of attacks like this with just the economic effort of finding new 0days, but not necessarily indeed. The developers of new vulnerabilities are commodities nowadays
- To one discovered attack of this type there are hundred never noticed
On the other hand it seems that big players of IT security are not understanding well the situation. Statements from Microsoft like "the attack was a a low-volume spear-phishing campaign directed at specific targets, not Windows users in general" are of course commercial statements aimed at reassuring the general users but actually they must frighten them because what is untold is:
- These attacks are among the most remunerative of the cybercrime scene
- They will not ever be totally disrupted, because the patch just removes the last and less important element,
- They are made to stay under the radar or detection being statistically irrelevant and meant to chirurgically hit their victims
- They are made to steal important assets
- OCG can hit any business, everywhere at anytime without being noticed
Is it enough to be worried? In my opinion absolutely yes.
[1] https://www.helpnetsecurity.com/2016/11/09/pawn-storm-windows-zero-day-patch/
P.S.: After the publication of this article another hot case has been reported. Also Lotus Blossom APT has been reported using it (see http://researchcenter.paloaltonetworks.com/2016/10/unit42-psa-conference-invite-used-lure-operation-lotus-blossom-actors/). Pawn Storm is not the only active group using these methods.
by Enrico Frumento (CEFRIEL)





