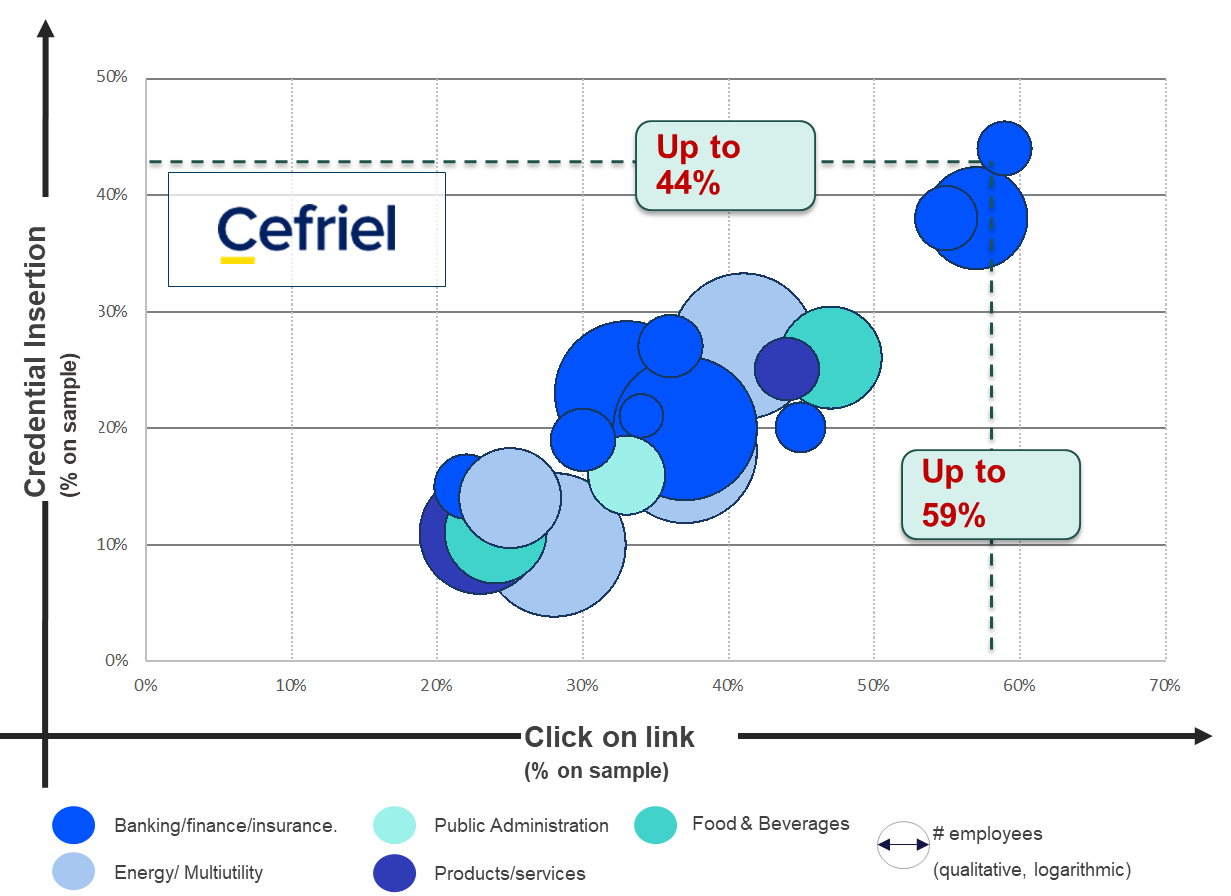
How many people accept being subjected to a social driven vulnerability assessment?
- Details
- Category: Social Engineering
- Published: Thursday, 04 October 2018 13:35

At a certain point, during the social engineering vulnerability assessment, the penetration tester and the company have to debrief the deceived persons, to share the results of the tests and transforms the whole experience in a positive one, also somehow delivering an awareness experience to the persons. Since the beginning of the field-tests we have had the wish to understand how many people would have accepted of being “victimized” by an SDVA test, even if it was for good...