What persuasion techniques are generally employed in phishing e-mails?
- Details
- Category: Social Engineering
- Published: Monday, 08 May 2017 11:19

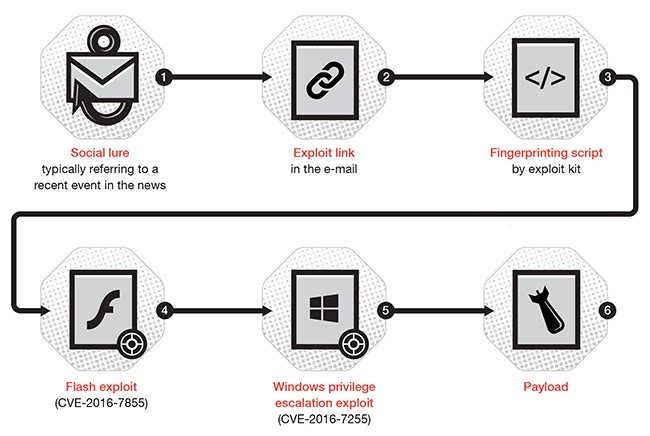
In this post we discuss what are the most influential persuasion techniques in phishing e-mails.
Social Engineering aims at manipulating users into performing undesirable actions, which likely lead to a data breach. Therefore, social engineering techniques are deeply rooted in psychology and, in particular, in persuasion techniques. Persuasion techniques have been widely studied in the literature, e.g., concerning marketing and politics.